TOR++ 一个强大的tor组合包
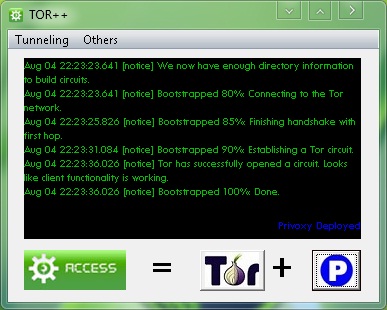
Many option for TOR combination.
Portable no .net framework needed.
Very easy for establishing connection on TOR network.
Q: What is TOR++ ?
A: Tor++ is a combination of 4 main tunneling software such as Polipo, Privoxy, Gpass, and Gtunnel which using the TOR engine to access the internet through TOR network.
Q: how to use it?
A:
* Download tor++
* Connect your PC in your ISP.
* Execute tor++, and wait until it build a TOR circuit.
* And now you can deploy the embedded tunneling software.
Q: How do I configure my browser.
A: Configuring your web browser is depend on what tunneling sw you’ve depoyed.
PRIVOXY 127.0.0.1:8000
POLIPO 127.0.0.1:8000
GPASS 127.0.0.1:8000
GTUNNEL 127.0.0.1:8081
Proxifier Directly No need
Note: I assigned privoxy, polipo and gpass on the same port so that it would be easy for us to
switch if we wanted. When you deploy GTUNNEL you dont need to configure your browser
it’s automatically configure and run browser for you.
Q: How about proxifier?
A: Running Proxifier is optional, if you dont want to configure your browser manualy then
* Run Proxifier as relay – you can use proxifier to tunnel you programs (AV, YM, amfrog, etc) on deployed tunneling sw.
Programs <–> Proxifier <–> Gpass/Polipo/Privoxy/Gtunnel <–> Tor <–> Internet
* Run Proxifier Directly – you can use proxifier to tunnel you programs (AV, YM, amfrog, etc) on TOR network directly.
Programs <–> Proxifier <–> Tor <–> Internet
Note: Source files will be extracted at C:\FBT. [kung gusto nyo likutin setting]
感谢AS网友推荐同时他还推荐了TORPlus组合包有兴趣的可以试试。

http://tiandixing.org/viewtopic.php?f=15&t=67373
“TORPlusBundle_2_2_32_1.zip…..”
(翻墙利器)
感谢支持呀
1.http://torvpn.com/information.html
2.http://shelltor.com/
3.http://mirror.tor.hu/
(翻墙利器)
shelltor.com收费的吧
1.http://www.masternewmedia.org/bypass_that_firewall/
2.https://www.gotroot.com/tiki-index.php?page=Anonymous+Bittorrent+with+TOR
“Note
This information is controversial, and some consider the use of bittorrent over TOR to be counter to the goals of the TOR project. This article does not seek to answer the questions about the validity of any protocol over the TOR network but merely how to do it. Also, be aware that the BT protocol itself my reveal a nodes real IP. Be informed about the technologies you use.
Instructions
To use Bittorrent with The Onion Skin Router (a project sponsored by the Electronic Frontier Foundation and previously funded by the Naval Research Lab), first, download and install The Onion Skin Router. You can download The Onion Skin Router from the following URL:
http://tor.eff.org/download.html (external link) (cache)
TOR is what makes your bittorrent traffic anonymous, TOR is a client that joins your system to the TOR anonymous network. This network is not a collection of proxies, its a low latency mix network, with SSL/TLS tunnels telescoped inside one another. This means that each system you route your traffic through can not see your traffic, or your IP address. If you want to understand how it does this, read The Onion Skin Router Wiki page for more information. Once you have The Onion Skin Router installed, and running, you can move on to the next step.
Install TOR client
The official installation instructions for TOR are available on the EFF TOR website:
http://tor.eff.org/cvs/tor/doc/tor-doc-win32.html (external link) (cache)
Instructions for Bittorrent clients that do not support TOR natively
Install Proxy Chains
Then, you need to download ProxyChains (external link) (cache). Unfortunately, this is currently only available for UNIX systems. If you are running Windows, you will want to use something other than TOR to use bittorrent anonymously, such as i2p or, you will want to use another bittorrent client that supports TOR natively. Currently, the official bittorrent client does not support TOR natively, but in the following section, we list clients that do. Or, as mentioned, you can use i2p to use bittorrent anonymously. Instructions for using i2p to make bittorrent anonymous are on the i2p wiki page.
Once ProxyChains? is installed, just add
socks5 127.0.0.1 9050
http localhost 8118
to the ProxyChains? config file at ~/.proxychains/proxychains.conf. Now that it is configured, type proxychains btdownloadcurses at the command line. Remember this, you must invoke proxychains to execute the bittorrent client for you. Do not start your bittorrent client without this if it does not support TOR natively and you have no configured it to do so!
Instructions for Bittorrent Clients that support TOR natively
List of clients that supports TOR natively
1. Azureus Bittorrent client
Download the Azureus Bittorrent client (external link) (cache) Instructions to configure this client to use TOR (external link) (cache)
Add in additional protections
Install Privoxy
This will help to ensure that your browser does not send information of its own accord to a website you want to visit anonymously. Like TOR, privoxy is an open source project, so no spyware or hidden code in this application and you don’t have to take our word for it, you can always check the source code yourself and compile from that trusted source if you prefer.
Download privoxy from here:
http://www.privoxy.org/ (external link) (cache)
Thats it!
If you installed TOR, privoxy and followed the instructions for configuring your client, you should be all set. Finally, please donate to the TOR project: http://tor.eff.org/donate.html.en (external link)
Contributors to this page: Michael Shinn20462 points .
Page last modified on Sunday 19 of October, 2008 21:22:48 EDT by Michael Shinn20462 points .
The content on this page is licensed under the terms of the Got Root License. ”
(翻墙利器)
感谢支持。。。
http://tor2web.org/
“Tor is a software project that lets you use the Internet anonymously. tor2web is a project to let Internet users access anonymous servers.
Here’s how it works: Imagine you’ve got something that you want to publish anonymously, like the Federalist Papers or leaked documents from a whistleblower. You publish them via HTTP using a Tor hidden service; that way your anonymity is protected. Then people access those documents through tor2web; that way anyone with a Web browser can see them.
Getting started
Whenever you see a URL like http://duskgytldkxiuqc6.onion/, that’s a Tor hidden Web service. Just replace .onion with .tor2web.org to use the tor2web proxy network. Example:
https://duskgytldkxiuqc6.tor2web.org/
This connects you with tor2web, which then talks to the hidden service via Tor and relays the response back to you.
WARNING: tor2web is only intended to protect publishers, not readers. You won’t get the level of anonymity, confidentiality, or authentication that you would get if you were using a Tor client yourself. Using tor2web trades off security for convenience; install Tor for better results. (More details…)
Example sites
Search Google
The Federalist Papers
WikiLeaks
More information
How do I run my own tor2web proxy?
Is this legal?
What about mirroring?
How can Tor make this better?
Support us
DONATE: Contribute via BitCoin at 1EkNYviucDXNiB7HsVZVuCi9FsvFFJu3tP
HOST: You can set up your own tor2web proxy.
CODE: You can write code to help us. Also check out tor2web-related tasks in Tor.
Press
Wired: New Service Makes Tor Anonymized Content Available to All
Ars Technica: tor2web brings anonymous Tor sites to the “regular” web
Tor blog: Quick thoughts on tor2web
info@tor2web.org”
(翻墙利器)
感谢支持。。
https://code.google.com/p/torsocks/
“Torsocks: use socks-friendly applications with Tor
Torsocks allows you to use most socks-friendly applications in a safe way with Tor. It ensures that DNS requests are handled safely and explicitly rejects UDP traffic from the application you’re using.
Torsocks is known to work on Linux and some distributions of Unix, including Mac OSX. Once you have installed torsocks, just launch it like so:
usewithtor [application]
So, for example you can use ssh to a some.ssh.com by doing:
usewithtor ssh username @ some.ssh.com
or launch pidgin by doing:
usewithtor pidgin
An alternative to usewithtor is torsocks:
torsocks pidgin
The tables below list applications that usewithtor/torsocks will send through Tor. At the moment a 100% guarantee of safe interoperability with Tor can only be given for a few of them. This is because the operation of the applications and the data they transmit has not been fully researched, so it is possible that a given application can leak user/system data at a level that neither Tor nor torsocks can control.
The following administrative applications are known to be compatible with usewithtor:
Application 100% Safe DNS Comments
ssh M Y Potential for identity leaks through login.
telnet M Y Potential for identity leaks through login and password.
svn M Y
gpg M Y gpg –refresh-keys works well enough.
The following messaging applications are known to be compatible with usewithtor:
Application 100% Safe DNS Comments
pidgin M Y Potential for identity leaks through login and password.
kopete M Y Potential for identity leaks through login and password.
konversation M Y Potential for identity leaks through login and password.
irssi M Y Potential for identity leaks through login and password.
silc M Y Potential for identity leaks through login and password.
The following email applications are known to be compatible with usewithtor:
Application 100% Safe DNS Comments
claws-mail M Y http://rorschachstagebuch.wordpress.com/2008/11/02/claws-mail-zweit-profil-fur-tor/
thunderbird N Y Probable identity leaks through javascript, mail headers. Potential for identity leaks through login, password.
The following file transfer applications are known to be compatible with usewithtor:
Application 100% Safe DNS Comments
wget N Y Probable identity leaks through http headers. Privoxy and polipo a better solution.
ftp M Y Passive mode works well generally.
Table legend:
DNS: DNS requests safe for Tor?
N – The application is known to leak DNS requests when used with torsocks.
Y – Testing has shown that application does not leak DNS requests.
100% Safe: Fully verified to have no interoperability issues with Tor?
N – Anonymity issues suspected, see comments column.
M – Safe enough in theory, but either not fully researched or anonymity can be compromised
through indiscreet use (e.g. email address, login, passwords).
Y – Application has been researched and documented to be safe with Tor.
Differences between torsocks and tsocks
A complete history of changes is maintained in the Changelog. The initial working copy of torsocks was obtained through the following steps in June 2008:
Tsocks was downloaded from the project’s sourceforge repository.
All patches listed at TSocksPatches in March 2008 were applied. In particular, the patch from Total Information Security that hooks DNS requests and passesthem to Tor. The original link for this patch is now dead and the authors are no longer available at the email addresses supplied in the patch’s source.
Weasel’s getpeername() patch and some build-related patches from Ruben Garcia were applied.
All references to tsocks in the project source files were renamed to torsocks.
The project was then migrated to an automake/autoconf build system.
To help with reconstructing the above steps a list of applied patches is available in the patches subdirectory of the torsocks source tree.
Enhancements unique to torsocks
The first release of torsocks contained the following enhancements:
Torifying reverse dns requests through gethostbyaddr()
Blocking of UDP traffic from sendto() and its variants.
Use of Tor-friendly defaults if no configuration file available.
The addition of all RFC defined private address ranges to the default configuration.”
https://code.google.com/p/torsocks/downloads/list
“torsocks-1.1.tar.gz.asc Torsocks 1.1 Signature Dec 11 198 bytes 206
torsocks-1.1.tar.gz Torsocks 1.1 Featured Dec 11 658 KB”
(翻墙利器)
感谢支持
我使用這個,tor++.exe的CPU佔用會高達40%,且長時間居高不下,不知到其他的朋友有沒有這個問題。
Dies ist ein haeufiges Problemm mit dem “software” auf dem Computer – der Konflikt.
(翻墙利器)
也许是
我也是
我也是,有时cpu占用一直是50%,楼主发的东东是不是有什么不兼容的问题,现在我都不大用了。
可能是有冲突,这个我没有做太多测试。
Blog.masked
http://ms4kc75hlvnfcxgz.onion/about
“everything you publish here is viewable on the world wide web @ masked.name
click a name to see their page, click the time to see that post
if you must refer to someone else with an account, use @name and it will link to them
if you must refer to a post made by someone else, use @name/id and it’ll link to it
don’t link to http://ms4kc75hlvnfcxgz.onion/ because this is viewed on the web, use the @s
use basic html tags, and please no scripting or attacks
Tags
bold
italic
I am seriously pissed off!
Oh sure, that’s what you say.
Check out this site. ”
http://ms4kc75hlvnfcxgz.onion/join
(4 hidden serices TOR – 翻墙利器)
网站打不开,不知道是做什么用的。
Gestern war alles gut,heute habe ich “504 Connect to oxtm3utqo54i7dtz.onion:80 failed: SOCKS error: host unreachable…..” – probieren Sie bitte noch Zeit zu Zeit.
(4 hidden serices TOR – 翻墙利器)
/German/
Entschuldigen Sie mir,dass ich einen Fehler gemacht habe.Es sollte sein “……von Zeit zu Zeit”
(4 hidden serices TOR – 翻墙利器)
/German/
呵呵,原来你说德语呀,那个网址只有使用Tor代理才能打开。
http://xqz3u5drneuzhaeo.onion/
“Hosting Features
Here you can get free hosting with PHP and MySQL
Unlimited Space
Unlimited Bandwidth
Unlimited MySQL Databases
Your own onion domain ( xxxxx.onion )
Fast Network with 24/7 Uptime
No javascript or cookies required to login
Upload a zip with your files and extract on server
FTP Access
No server logs of any kind
NO BACKUPS if our drive fails, all data will be lost, backup yourself if its important.
What’s Allowed
We do not give permission for upload of any illegal files.
If you chose to do so anyway, we are not responsible for your actions.
I’ve not got a infinite hard drive and the server cpu is limited so please don’t upload too much or use resource intensive scripts.
Need Help?
When installing some php scripts it might complain about chmod, disabled functions or safe mode, just ignore the warning and continue anyway.
If the php warnings display on your site, edit the php file and find the line it complains about and put an @ before the function it complains about. eg. change chmod to @chmod etc…
If it still wont work then use the Contact link above or reply to our thread on onionforum
News May 2010
New 8 core i7 server, more ram, more bandwidth, should improve recent slowness.”
http://xqz3u5drneuzhaeo.onion/cpanel/register.php
(3 hidden serices TOR – 翻墙利器)
感谢支持,打不开。
http://z6gw6skubmo2pj43.onion/
http://z6gw6skubmo2pj43.onion/www/pages/home.html
“The HiddenTracker is a bittorrent tracker free for anyone to use. To protect the people who maintain it, it runs behind a Tor hidden service. You don’t need to register, upload or index a torrent anywhere, all you have to do is to include a HiddenTracker tracker URL in your torrent, and share it with whoever wants like to download it.
Getting Started
You can get started using the HiddenTracker without installing any software, or configuring anything. When you create or download a torrent file, simply add the following two of our HiddenTracker announce URIs:
http://z6gw6skubmo2pj43.onion:8080/announce https://kg6zclbtm7kwqide.tor2web.org/announce
While that’ll get you started, you’ll get better performance with some configuration changes. In addition, for redundancy, we have a number of different addresses, so that the service stays up even when some of our servers go down. Check out the instructions for for details on how to get the best performance out of the HiddenTracker.
More Info
For more information on what we do, and why we do it, please read all about us. You can read more about how Tor protects privacy and anonymiy on the Tor Project’s website. ”
http://z6gw6skubmo2pj43.onion/www/pages/about.html
“Contact
You can get in touch with us at thehiddentracker@gmail.com. For secure communications, please use our GPG public key.
Check out @hiddentracker on Twitter. We’ll try to keep updates infrequent, so that we don’t clog up your news feed.
About Us
The HiddenTracker is a BitTorrent tracker. We use the open source OpenTracker software, like the late Pirate Bay tracker. A Tor hidden service allows us to to maintain our superhero-like hidden identities. In addition to giving us an exotic air of mystique, keeping the location of our servers hidden helps us to protect ourselves and the service from various sorts of attacks, especially baseless legal threats that we can’t do anything about.
Abuse
If you have a complaint about our service, please let us know. However, please be aware that it is very unlikely that we’ll be able to do very much. In particular, we can’t remove a torrent’s info-hash from the tracker. Not only do we have no idea what content a perticular info-hash pertains to, our software is not configured ot let us much about with individual torrents.
Volunteers
We can probably use all the help we can get. Whether you can donate time, expertise, money or moral support, we’d really appreciate it. Please get in touch.
Access
You can access the website via three Tor hidden service addresses:
z6gw6skubmo2pj43.onion
neexikvlji6hkefm.onion
gfkrrnmecmfqwpjf.onion
In the unlikely event that you’re not a Tor super user, you can replace the “.onion” in the address with “.tor2web.org”, to access the website via a normal web browser. This trick will work for the website, but not for the tracker, since Tor2Web only proxies port 80. We have other announce addresses for use with Tor2Web, which are listed in the setup instructions, along with our purely hidden service announce addresses.
We may from time to time add or remove hidden service addresses as our server configuration changes. If we publish HS addresses anywhere but here, we’ll be sure sign then. ”
翻墙利器
哦,明白了,只有用tor代理才能打开的网站
http://4eiruntyxxbgfv7o.onion/pm/
“Welcome to TorPM! A popular secure messaging service for use over Tor.
PM means Private Messaging. This service allows members to communicate with each other privately. Like e-mail, but for Tor users.
NEW: Now compatible with HiddenMessaging service. To send a message to HiddenMessaging users, use username@hiddenmessaging. HiddenMessaging users can also contact TorPM users by using username@torpm
Features:
AES Encryption
All messages are stored on a AES-encrypted container [Details]
No data retention
When you empty your inbox, all messages are overwritten to prevent data recovery [Details]
Cookie free
Requires no cookies, java, or javascript.
Sign up now, or Log in to check your messages ”
http://4eiruntyxxbgfv7o.onion/pm/signup.html
翻墙利器
ssh91.com就要ssh开始限量提供免费vpn账号,每月3G流量,限制50个名额!
呵呵,你是想让我发博客给你做宣传还是…?